Links to each section:
Part 1 - (Un)boring intro with all the snazzy info
Part 2 - Setup your second partition
Part 3 - Setup your first partition (sounds backwards, I know) -- you are here
Part 4 - Other cool stuff -- COMING SOON
Part 3 - Setup your first partition
~So now that you have copied your operating system from Partition 1 to the inner volume of Partition 2 we need to securely wipe the contents of Partition 1. Otherwise, even if you reinstall Windows on Partition 1, someone with forensic capabilities may be able to recover the previous Windows installation Partition 1 and thereby build a case that you have a hidden operating system, etc.
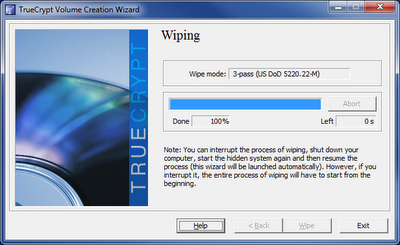
~Using
the default Department of Defense standard of 3 passes of random ones
and zeros for wiping is quite adequate in my opinion. For utter
paranoia, try additional passes -- though that could put your wipe time
at days or weeks!...
~Click Wipe:
~Click OK here:
~More mouse fun! The more you move your mouse, the more securely and randomly Partition 1 will be wiped!
~Wiping
in some cases can take all day/night, even at 3 passes. Other factors
of course include the size and speed of your drive.
~Here is the success dialog:
~Click Exit:
~So
now it is time to go ahead and install a fresh copy of Windows on
Partition 1 as a decoy operating system. Just pop a Windows disc in
there and install on Partition 1. (Don't accidentally install onto or
delete Partition 2!!) Once that's done, download TrueCrypt onto the
fresh decoy install and choose Create Volume. Then choose Normal since
this will be the decoy installation and press Next:
~Choose Encrypt the Windows system partition...
~Choose Single-boot
~Make
sure you select the same encryption algorithm here that you did when
you created the inner volume on Partition 2. They must be the same
because both the decoy and hidden operating systems use the same
bootloader and there is a different bootloader for each algorithm.
~More mouse fun! Great to feel like you are a part of the process, huh? :-) Move that mouse for the greater good of your encryption strength!
~Click Next...
~Somewhere
in there it asks you for the password. Can't remember at which point.
(Oopsie.) Anyway, when it does, you need to enter Password A for the
decoy operating system. Do you need any more sermons about secure
passphrases and whatnot? Didn't think so. ;)
~It
will also ask you about creating a rescue disc. Creating a rescue disc
is pretty important, as you can see below. It might sound scary to have
it laying around, but your system will still require the password even
when using the rescue disc. It's not really a vulnerability any more
than the presence of the bootloader itself which is put on your hard
drive. Just make sure you
put it in a safe place so you don't lose it.
~TrueCrypt creates an ISO and then helps you burn it to optical media as a rescue disc:
~The rescue disc is verified to make sure it was a good burn:
~Now
we are going to tell TrueCrypt how we want the data wiped from
Partition 1. Wiped again, you say? Yup. The last time we wiped Partition
1 was to wipe operating system from it that was copied to the inner
volume of Partition 2. This time TrueCrypt is going to encrypt the decoy
operating system and wipe the unencrypted version of it. If it didn't,
then someone could potentially do forensics on Partition 1 and recover
the unencrypted version of the decoy operating system. This would be
especially bad for those who use their decoy system for activities which
are of a lower level of sensitivity but sensitive, nevertheless. As
stated earlier, the default of 3 passes should be quite adequate.
~As stated, this will take a while once it actually starts which will happen later...
~TrueCrypt is going to test everything before doing the final encryption and wipe. Click Test:
~TrueCrypt
informs you that this is not the real thing and that actual encryption
will not take place. However, if the test fails, then Window may fail to
start. If this does occur, you can come back here and read the various
options for repair. Hopefully, you will be good though.
~I scrolled down and took another photo:
~Time
to test, then. Click Yes and then when your computer reboots it will
prompt you for Password A. If you have any trouble, see the 2 previous
images.
~After you've rebooted and typed Password A, hopefully
this is what you are now looking at. TrueCrypt warns here that in the
event of power loss or a system crash during the encryption process, data on the decoy operating
system may be gone forever. I didn't mention backups sooner
because I am assuming that you followed my advice in Part 2 and used a clean
system with a fresh Windows install. So hopefully, you don't even need backups.
If you do, read the instructions here on how to defer, backup data and then
resume. If you don't need to make backups, then click Encrypt.
~The
next 3 photos provide instructions on how to troubleshoot any potential
future booting issues with the rescue disc... Press OK.
~TrueCrypt
is now encrypting your decoy operating system on Partition 1! Folks,
this is even more amazing than it may seem. It's actually quite
remarkable. Think about it. What's happening here is that while booted into Windows (not a live environment!) TrueCrypt is encrypting the currently booted Windows AND wiping the non-encrypted version of it
all on the fly without even rebooting. WHAT? How is that even possible?
It's more magic from the TrueCrypt people!! If this doesn't make you
feel like donating, what will???!!!
~If
you want, you can setup additional non-system encrypted volumes to be
mounted at boot up, but that is outside the scope of this article.
~You can click Do not show this again here:
~But if you had clicked Show more information you would have seen this, which was shown earlier -- so not that big of a deal.
~Alright,
let's test this baby! If you reboot, you should get the bootloader shown
below. If you type Password A, you get the decoy operating system on
Partition 1. If you type Password B, you will get the hidden operating
system on the inner volume of Partition 2! Don't worry, if you press
Escape it doesn't really bypass authentication as long as you have
encrypted the drive (which you just did.) It would only work if you had a
TrueCrypt bootloader sitting on top of an unencrypted system, which is not the case here.
~If
instead of typing the password or Escape you press F8, you will get
some options which you will hopefully never need. Most of these options
are only there because this same bootloader gets copied to the rescue
disc and would be run from there.
Links to each section:
Part 1 - (Un)boring intro with all the snazzy info
Part 2 - Setup your second partition
Part 3 - Setup your first partition (sounds backwards, I know) -- you are here
Part 4 - Other cool stuff -- COMING SOON

































No comments:
Post a Comment
Spammy/foul language comments or those with an explicit avatar will be tossed in a 55 gallon drum and a match thrown in after them. (Oooo, now I can warm my hands!!)